Ridgeback: Active Defense for Modern Threats
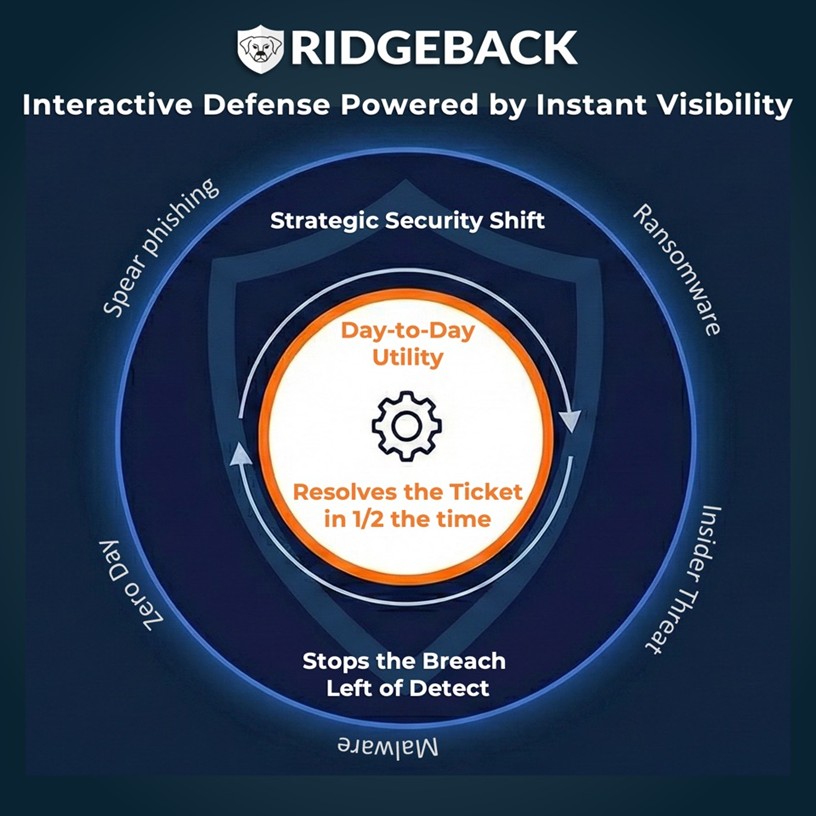
In today’s AI-enabled threat landscape, the value of a security tool is measured by its operational impact and control effectiveness rather than just its feature list. Ridgeback breaks traditional evaluation molds by providing an easy-to-operationalize solution that works within your existing environment – whether a global largest enterprise or a small, stretched local businesses – to disrupt adversaries in real-time.
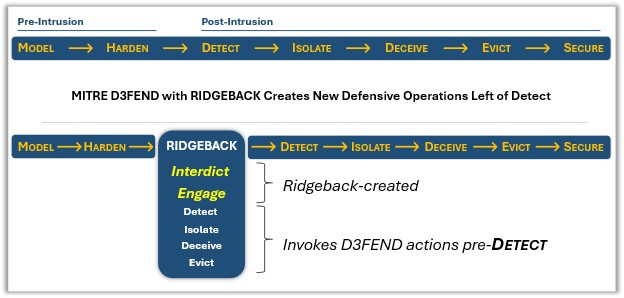
Gartner cites the need for a new generation of preemptive security tools. Ridgeback is the leader in applying the Gartner standards of “deny, deceive and disrupt” to cybersecurity.
Rapid Deployment and Operational Ease
Ridgeback is designed for immediate utility, requiring no agents on endpoints and minimal ongoing administration.
Comprehensive Network Visibility
Achieve 100% visibility across all network layers and device types without requiring complex routing changes.
Efficiency in Complex Systems
Ridgeback helps IT and security teams transform chaotic environments into orderly systems, drastically reducing the time required to identify issues and contain threats.
High-Fidelity Sensing
By focusing on actual adversary interaction rather than mere inference, Ridgeback delivers high-fidelity signals with virtually no false positives.
Automated Containment and Disruption
Ridgeback imposes high costs on attackers by presenting Phantom on-the-fly, on-demand to engage, discover, and halt lateral movement.
Compliance and Control Validation
Meet regulatory requirements and validate Zero Trust architectures through continuous, real-time evidence production.
Business and Financial Impact
Beyond security, Ridgeback optimizes your operations by saving analyst hours and de-emphasizing redundant tools.
The Active Defense Advantage
Ridgeback fills the blind spots created by traditional EDR, NDR, and UBA solutions, providing instant containment at the network layer.
Ridgeback offers a non-disruptive, agentless solution that provides 100% network visibility and instant, automated containment, significantly reducing both breach probability and operational overhead.